Setup DVWA to Practice Application Security Pentesting
DVWA is a purposefully built “vulnerable” web application designed to teach Application Security pentesting.
This guide will show you how to install and configure DVWA.
LAMP Stack Base Setup
If you haven’t already done so, setup a LAMP stack
You will need to remove the default index.html page. Login via SSH and run the following command:
sudo rm -rf /var/www/html/index.html
Setup DVWA Database
The DVWA needs a database. To create one, login to mysql and add a user called dvwa. You’ll need your password when you edit config files, so save it.
sudo mysql -u root -p
create database dvwa;
grant all on dvwa.* to dvwa@localhost identified by 'SuperSecret(P@ssW0rd)';
flush privileges;
quit
Download DVWA
The project is hosted on GIT and is downloaded with your favorite git client (command line example to download into the /tmp/DVWA location):
git clone https://github.com/ethicalhack3r/DVWA /tmp/DVWA
Cloning into '/tmp/DVWA'...
remote: Enumerating objects: 3022, done.
remote: Total 3022 (delta 0), reused 0 (delta 0), pack-reused 3022
Receiving objects: 100% (3022/3022), 1.52 MiB | 896.00 KiB/s, done.
Resolving deltas: 100% (1329/1329), done.
Install DVWA
Simply copy the files to the proper location on your web server. If you used the LAMP stack setup guide above for Ubuntu 18.04 LTS, that would be:
sudo rsync -avP /tmp/DVWA/ /var/www/html/
Create Config File
The configuration file for your DVWA install needs to be
sudo cp /var/www/html/config/config.inc.php.dist /var/www/html/config/config.inc.php
Update Config File
Next you’ll need to update the config settings file so it knows how to connect to the database you just created.
sudo vim /var/www/html/config/config.inc.php
$_DVWA[ 'db_server' ] = '127.0.0.1';
$_DVWA[ 'db_database' ] = 'dvwa';
$_DVWA[ 'db_user' ] = 'dvwa';
$_DVWA[ 'db_password' ] = 'SuperSecret(P@ssW0rd)';
Read through the config file for the other options you can change, such as testing captchas.
Make PHP More Vulnerable
DVWA demonstrates vulnerabilities in PHP (among other things). In order to go through these tutorials on PHP vulnerabilities, you will need to make sure the PHP portion of your LAMP server is insecure.
sudo vim /etc/php/7.2/apache2/php.ini
Make the following changes:
allow_url_include = on # – Allows for Remote File Inclusions (RFI)
allow_url_fopen = on # – Allows for Remote File Inclusions (RFI)
safe_mode = off # – (If PHP <= v5.4) Allows for SQL Injection (SQLi)
magic_quotes_gpc = off # – (If PHP <= v5.4) Allows for SQL Injection (SQLi)
display_errors = off # – (Optional) Hides PHP warning messages to make it less verbose
Create Insecure File Permissions
DVA Needs access to the following locations to demonstrate the file permissions flaws:
/var/www/html/hackable/uploads/
/var/www/html/external/phpids/0.6/lib/IDS/tmp/phpids_log.txt
To set these up with permissive file permissions that the web server can manipulate, you change ownership using the chown command:
sudo chown -R www-data.www-data /var/www/html/hackable/uploads/
sudo chown -R www-data.www-data /var/www/html/external/phpids/0.6/lib/IDS/tmp/phpids_log.txt
sudo chown -R www-data.www-data /var/www/html/config/
Test Your Setup
Visit the IP of your server in a browser to see what else you need to setup:
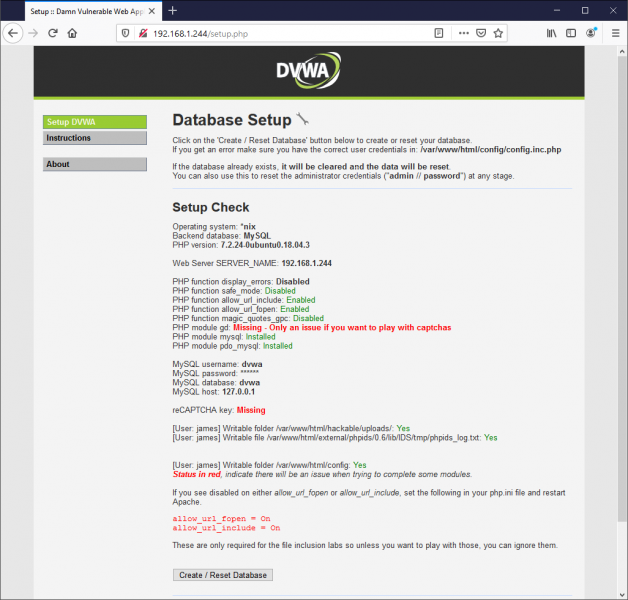
Create DB using DVWA Setup
If everything looks good, go ahead and create your database:
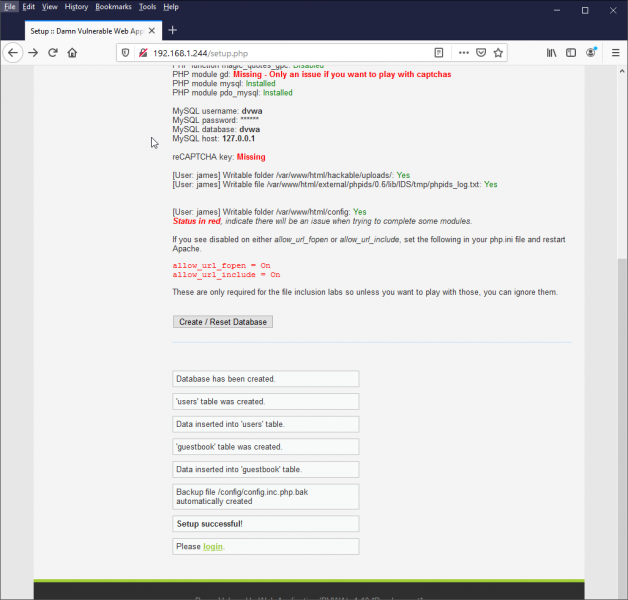
Login with admin/password
The default user/pass is admin/password.
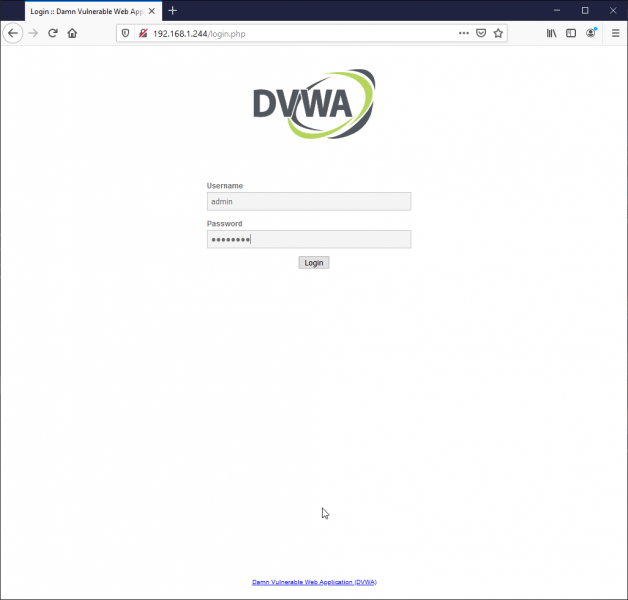
Begin Using DVWA
Read the instructions and tutorials and go through the OWASP top 10 list provided by this awesome DVWA tutorial.