How to Troubleshoot SIC on Check Point Firewall
SIC (Secure Internal Communication) is used to establish trust between firewalls and managers. This is how to troubleshoot SIC:
SIC is actually a certificate based challenge, and the cert is generated by the one time password process. SIC is based on SSL with digital certificates. The CA (certificate authority) is created when the manager is installed. This CA issues certs afterwards to all processes/servers that communicate using SIC. Basically SIC establishes trust and allows the gateway to communicate with other Check Point devices that possess a SIC certificate, signed by the same ICA.
Check Point Support Center
There is an article on the Check Point support site that describes other things to look at relating to SIC: SK30579
Ports Related to SIC
Port 18209
Used for communication between the Security Gateway and the CA for status, to issue, and revoke.
Port 18210
Used to pull certificates from the CA.
Port 18211
Used by the cpd daemon on the Security Gateway to receive the Certificate (by clicking "Initialize" in SmartDashboard).
Basic SIC Troubleshooting
Make sure the routes and connectivity exist between the gateway and Security Management Server.
Allow any rules or ACLs that might block communication.
Make sure server and gateway use the same SIC key.
Verify date and time are accurate on both devices.
Remote gateways need the /etc/hosts IP/name to resolve the management IP
SIC Related Processes
CPD is used for the SIC process. In the process of start/stopping CPD to debug SIC, you could affect the following services:
Policy Fetch/Installation
SIC (sic of course)
Messaging for other SmartCenter Daemons
Licensing
CPD can sometimes consume all available memory. Check the output of the “top” command (look at RES and CPU columns):
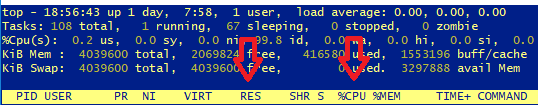
Restarting CPD Process
`
# cpwd_admin stop -name CPD -path "$CPDIR/bin/cpd_admin" -command "cpd_admin stop"
# cpwd_admin start -name CPD -path "$CPDIR/bin/cpd" -command "cpd"
`
Inspect SIC Packets with FW Monitor
`
fw monitor -e 'accept (dport=18209 or dport=18210 or dport=18211);'
`
What to look for:
Look at the i I o O chain to tell interface entrance/exit or if it hits firewall at all
If it goes through part of the i I o O chain but not all, it is dropped on the firewall and the drop may appear in the logs
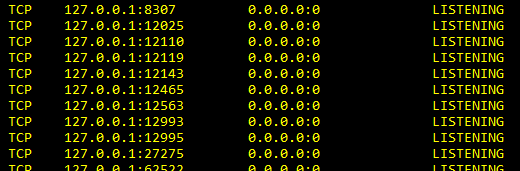
Verify SIC Service is Listening
`
(windows)c:\> netstat -na | findstr 18211
(linux)expert# netstat -na | grep 18211
`
Error Messages Related to SIC
Failure to Initialize SIC
sk12688
Failed to connect the module
sk35200
Policy install fails on a rebuilt VSX cluster member
sk25542
SIC Status for not communicating. Peer does not have a certificate for SIC
sk37295
Rmote Security gateway does not receive the certificate
SIC General Failure
sk37219
CPD process consumes high CPU during SIC status test
sk16200
SIC general failure error no. 148
sk32715
CPD reaches high CPU after install QoS Policy with User Access
SIC Error no. 147
sk36082
Installing Policy to a VPN-1 gateway from a CMA fails with SIC error 147
sk33849
CPD debug shows: "SIC Error for CpdPing: received bad message length from peer"
sk33764
SIC Status for Not communicating Authentication error err no 147
Misc SIC Errors
sk43744
Automatic SIC renewal mechanism does not function in R70.xx
sk42916
Security Gateway randomly loses SIC with SmartCenter
sk44272
Undefined Error in SmartDashboard when establing Trust with Virtual Device
sk32183
SIC fails even though SIC certificate was renewed